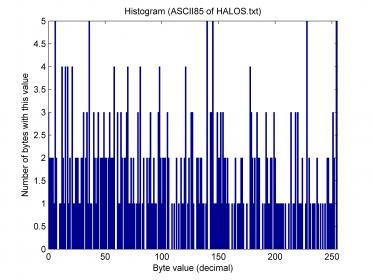
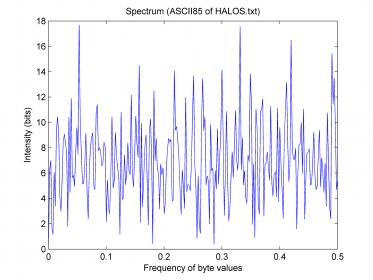
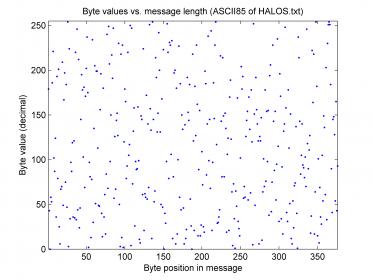
Oh dear, I’m sorry I couldn’t reply sooner, but please allow me to clear this up now before there is any more speculation:
In that post you’re referring to, I presented a solution based on my own experiences on this forum earlier this year (2013). My forum account was disabled for 3-4 months after I tried changing the email address in my profile, and the forum just wouldn’t send me any confirmation emails (tried four different email addresses). I’m pretty sure there must have been some sort of issue with the forum, since the forum page would hang for like 20-30 seconds after clicking the save settings button on the “edit password/email” page. I made another attempt in July and finally received the confirmation email so that I could confirm the email change and reactivate my account. It’s a bit odd that it wasn’t reported on the forums, perhaps it only affected a few users. I couldn’t post/PM about it myself, since my account was in a disabled state, awaiting confirmation.
I’m just a regular user here, who happens to be interested in the ARG, and cares about it. That’s all.
However, I should probably remove/change my avatar picture, which I recently added. I have to admit I was a bit worried that something like this might happen when I chose that particular picture, given this context, but I figured I’d just keep it until I found something better. I sincerely apologize if anyone was misled to believe that I had some inside knowledge and was dropping clues here. That was not my intention.
I hope this clears up any confusion.